Introduction:
Enabling rapid querying of user information, the Lightweight Directory Access Protocol (LDAP) is a protocol facilitating applications to swiftly retrieve essential data.
Within your office, a colleague aims to accomplish two tasks: emailing a recent hire and obtaining a printed record of the discussion from a new printer. Leveraging LDAP (Lightweight Directory Access Protocol) enables the realization of both actions.
With correct configuration, the employee can achieve these tasks seamlessly without requiring IT intervention.
What Is LDAP?
Usernames, passwords, email addresses, printer connections, and other unchanging information find storage in company directories. Open and vendor-neutral, LDAP serves as an application protocol to access and manage this data. Additionally, LDAP handles authentication, enabling users to log in once and access a multitude of files on the server.
Functioning as a protocol, LDAP doesn’t dictate the operational details of directory programs. Instead, it operates as a language variant, facilitating users in swiftly locating the required information.
Being vendor-neutral, LDAP is compatible with various directory programs, offering versatility in its application. Data found within a directory typically encompasses:
Descriptive. Multiple points, such as name and location, come together to define an asset.
Static: The information doesn’t change much, and when it does, the shifts are subtle.
Valuable: Data stored within the directory is critical to core business functions, and it’s touched over and over again.
At times, individuals incorporate LDAP in collaboration with other systems during their workday. For instance, your staff might utilize LDAP to establish connections with printers or authenticate passwords. Subsequently, these employees might transition to Google for email services, where LDAP plays no part.
The LDAP Process Explained:
Throughout the workday, the average employee engages with LDAP frequently, often without realizing the connection’s occurrence despite the intricate and complex steps involved.
An LDAP query typically encompasses the following stages:
- Session Connection: The user establishes a connection with the server via an LDAP port.
- Request: Users submit queries, like email lookups, to the server.
- Response: The LDAP protocol queries the directory, retrieves the required information, and delivers it to the user.
- Completion: The user disconnects from the LDAP port.
Although the search process may appear simple, a significant amount of coding underpins its functionality. Developers need to define search size limits, server processing time, variable inclusion in searches, and more.
For individuals transitioning between different companies, LDAP searches may be performed at each location. However, the search mechanics and functionality can differ considerably based on LDAP configurations.
Before any search initiation, user authentication is a prerequisite for LDAP. Two authentication methods are available:
- Simple: The user connects to the server using the correct credentials.
- Simple Authentication and Security Layer (SASL): Advanced security-demanding companies utilize a secondary service like Kerberos for user authentication before connecting.
Queries can originate within the company’s premises or even from mobile devices and home computers. A majority of LDAP communication occurs without encryption, potentially posing security risks. To address this, most companies implement Transport Layer Security (TLS) to safeguard LDAP messages.
LDAP offers a wide range of operations, including:
- Add: Insert a new file into the database.
- Delete: Remove a file from the database.
- Search: Initiate a query to retrieve information from the database.
- Compare: Analyze two files for differences or similarities.
- Modify: Make changes to existing entries.
An example DN for example.com could look like this:
["uniqueIdentifier=85317,dc=person,s=state,c=us,dc=example,dc=com"]
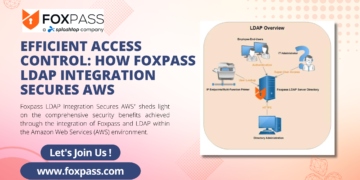
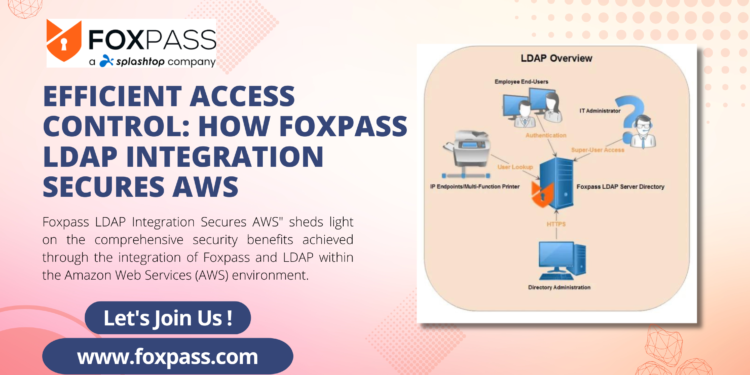
Foxpass LDAP Integration Secures AWS:
Foxpass AWS LDAP, Integration Secures AWS” sheds light on the comprehensive security benefits achieved through the integration of Foxpass and LDAP within the Amazon Web Services (AWS) environment.
In the realm of cloud-based infrastructure and remote access, the title highlights the pivotal role played by Foxpass and LDAP in enhancing the security landscape of AWS. By combining the robust features of Foxpass with the proven capabilities of LDAP, organizations can establish a formidable defense against unauthorized access, data breaches, and other security vulnerabilities.
The content elaborates on how Foxpass LDAP integration bolsters user authentication and access control, making it possible to seamlessly manage user privileges and permissions within AWS environments. Additionally, the article may delve into the role of LDAP in user directory management, highlighting its ability to centralize and streamline user information across the organization.
Foxpass comes packaged within a straight-forward dashboard that makes assigning groups and permissions for your employees way easier than OpenLDAP.
With Foxpass you can implement an easy-to-use Cloud LDAP solution in minutes–not days or weeks.
Conclusion:
Discover the power of Lightweight Directory Access Protocol (LDAP) in modern business operations. This comprehensive exploration highlights LDAP’s role in seamless user information retrieval and secure authentication processes. Learn how LDAP collaborates with systems like Foxpass to reinforce security, particularly in AWS environments. Explore its adaptability, ease of integration, and effectiveness in streamlining user management and enhancing data security. Uncover how the convergence of cutting-edge technology and robust security practices in Foxpass LDAP Integration paves the way for innovative security solutions in today’s interconnected business landscape. Elevate your data protection and streamline operations with this forward-looking security solution.